Cross-Site Scripting via File Upload in Koha (CVE-2026-26378)
Contents
Cross-Site Scripting via File Upload in Koha (CVE-2026-26378)
Description and Impact
| Type | Version Affected | ?-day |
|---|---|---|
| XSS via File Upload | ≤ 25.11 (latest) | 0-day |
Steps to Reproduce
First, create an arbitrary vendor (if one already exists, skip this step):
Vendor ABC was successfully created.
Access Receive Shipments to create a new Invoice:
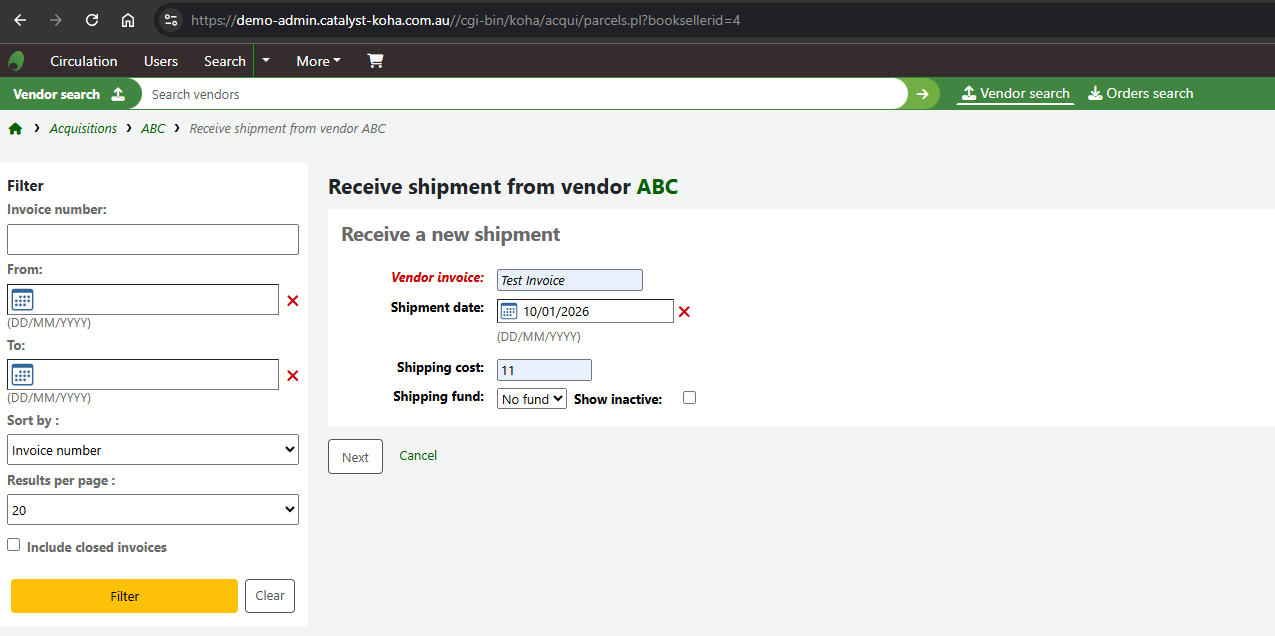
Successfully created an Invoice with invoiceid=3 :
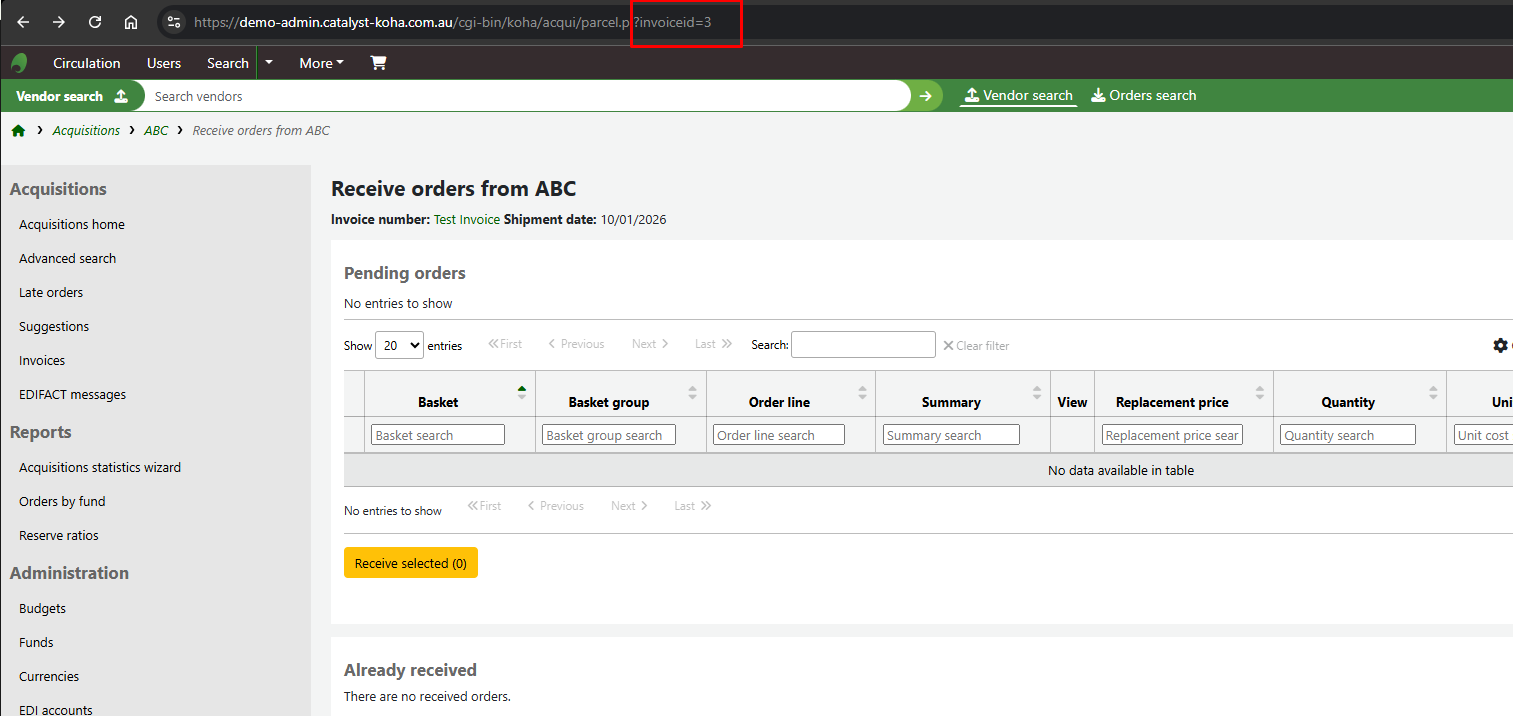
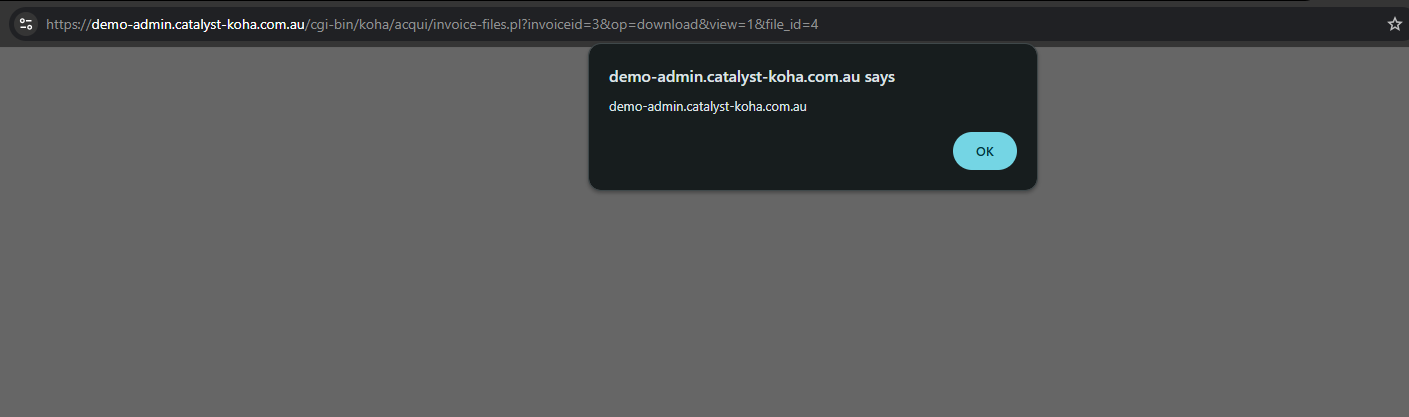
Then, access the URL: cgi-bin/koha/acqui/invoice-files.pl?invoiceid=3 :
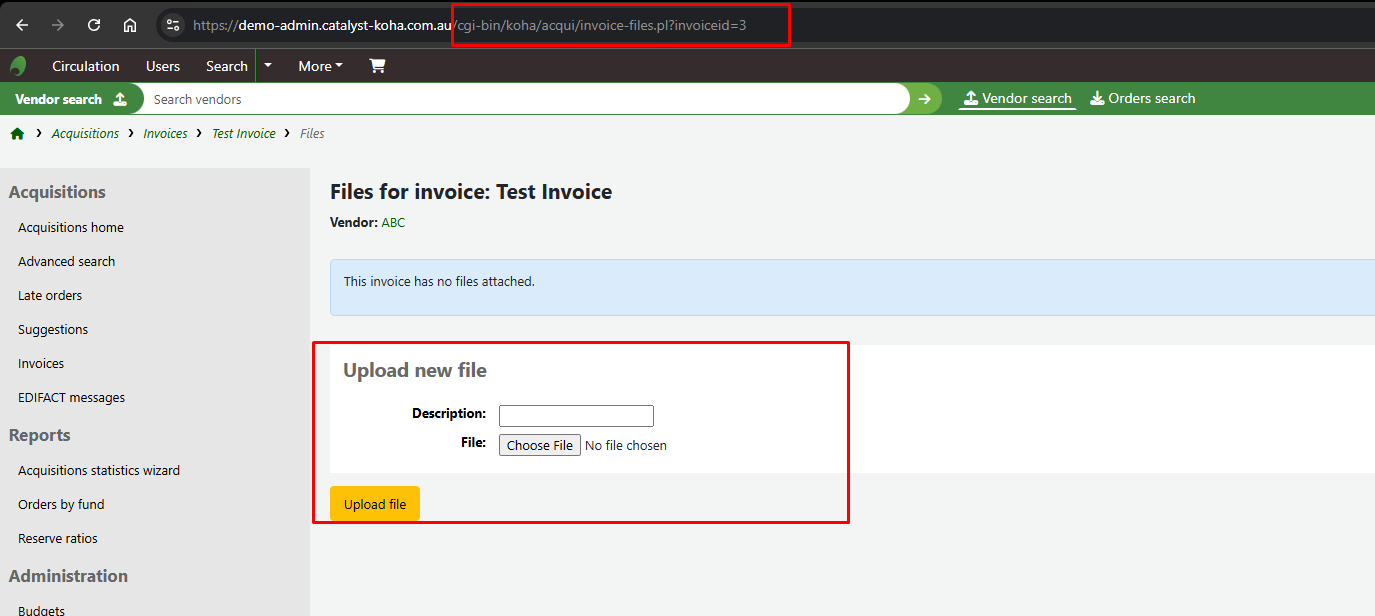
Proceed to upload an SVG file containing the XSS payload as follows:
<svg xmlns="http://www.w3.org/2000/svg" onload="alert(document.domain)"></svg>
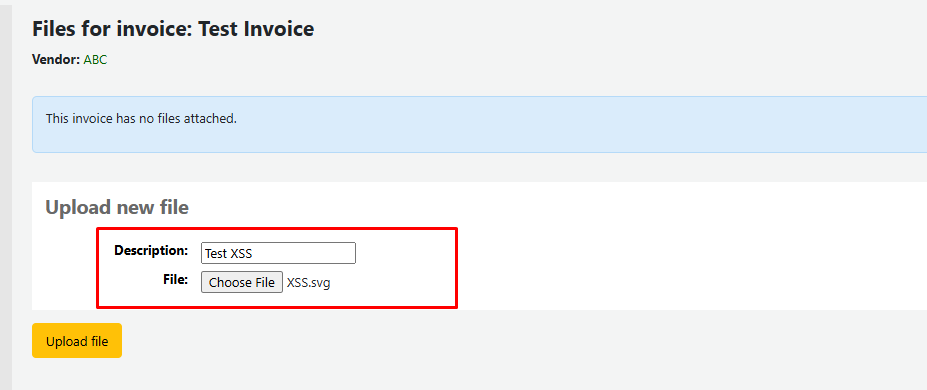
Since the application allows inline rendering for files with an image Content-Type, it is possible to upload an SVG file containing an XSS payload. Clicking to view the file will cause the JavaScript to execute in the browser → Triggering XSS.